+ Average beginner/intermediate VM, only a few twists |
| + May find it easy/hard (depends on YOUR background) |
| + ...also which way you attack the boxhttps://www.vulnhub.com/entry/stapler-1,150/
“know yourself and you will win all battles”
― Sun Tzu
Enumeration
Let’s use NMAP to enumerate.


Brooding:🤔
This machine has many services running. First thing is to rule out the unnecessary services.
Ruling out ports
- Port 666 sent out a zip file having an image.

📌 username: scott
2. Port 20 — Nothing here.
3. Port 22 — No available exploits.
4. Port 53 — Found nothing on DNS — all the available exploits are DOS.
5. Port 3306 — There is not remote exploit and no default pwd.
More Enumeration 🤓…
- port 21
📌 username:harry


📌username:elly
📌username:john
2. port 80
- There is no trial on manual walk + source code view + robots.txt
- Nikto scan

Nothing on .bashrc and .profile
🔑 It says that it web server might be mounting a user directory. 🤔
- Gobuster — Nothing here.
3. port 12380
- manual walk + source code view + robots.txt
📌 username:zoe
User-agent: *
Disallow: /admin112233/
Disallow: /blogblog/
- Nikto scan

- Gobuster

Found a blog:
https://192.168.103.171:12380/blogblog/
Apache[2.4.18], Bootstrap[20120205,4.2.1], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[192.168.103.171], JQuery, MetaGenerator[WordPress 4.2.1], PoweredBy[WordPress,WordPress,], Script[text/javascript], Title[Initech | Office Life], UncommonHeaders[dave], WordPress[4.2.1], x-pingback[https://192.168.103.171:12380/blogblog/xmlrpc.php]
Nothing vulnerable on wordpress.
4. port 139
Found few shared folders.
- Got a wordpress backup — kathy
- Got todo file — kathy
📌 username:kathy
Got users through Enum4Lin script.

Let’s try these users on the services…
- ftp
- ssh
- wordpress
Finding POI(Point Of Intrusion)
Use the usernames to brute-force since we have no other way to get in for now.


No luck on other services.
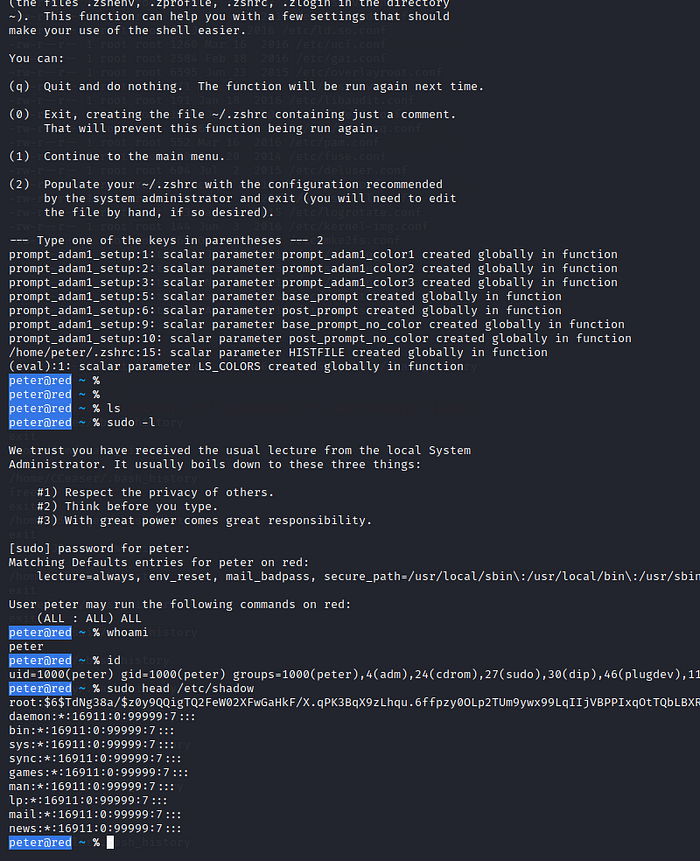
Exploitation

Privilege Escalation
After looking into the .bash_history file🤓, got the credentials for other 2 accounts. one of the account has all the priv.